RECENT POSTS
- AIL v6.6 – Advanced PDF Processing and Manual Crawling Support
- AIL v6.5 – I2P Crawler, Image Descriptions, and Enhanced Search
- AIL v6.4 Release Notes with Mail Search functionality, improved crawling capabilities and many bugs fixes
- AIL v6.3 – Passive SSH Integration for Onion Correlation and Deanonymization
- AIL 6.2: Smarter Analysis, Search and Enhanced User Experience
- The Art of Pivoting - How You Can Discover More from Adversaries with Existing Information
- AIL Project v6.1 released with new features including unsafe filter for Tor crawling, many bugs fixed and Telegram attachment analysis (2025-02-06)
- AIL Project v6.0.1 - Improved usability in social network monitoring and many bugs fixed
- AIL Project v6.0: Improved Dark Web Analysis with a New Dashboard
- AIL Framework v5.9 Released – New Features such as dom-hash correlation, improvements and many bug fixes
- All posts ...
AIL framework 5.2 released with new features and various bugs fixed
Jul 12, 2023 • adulau
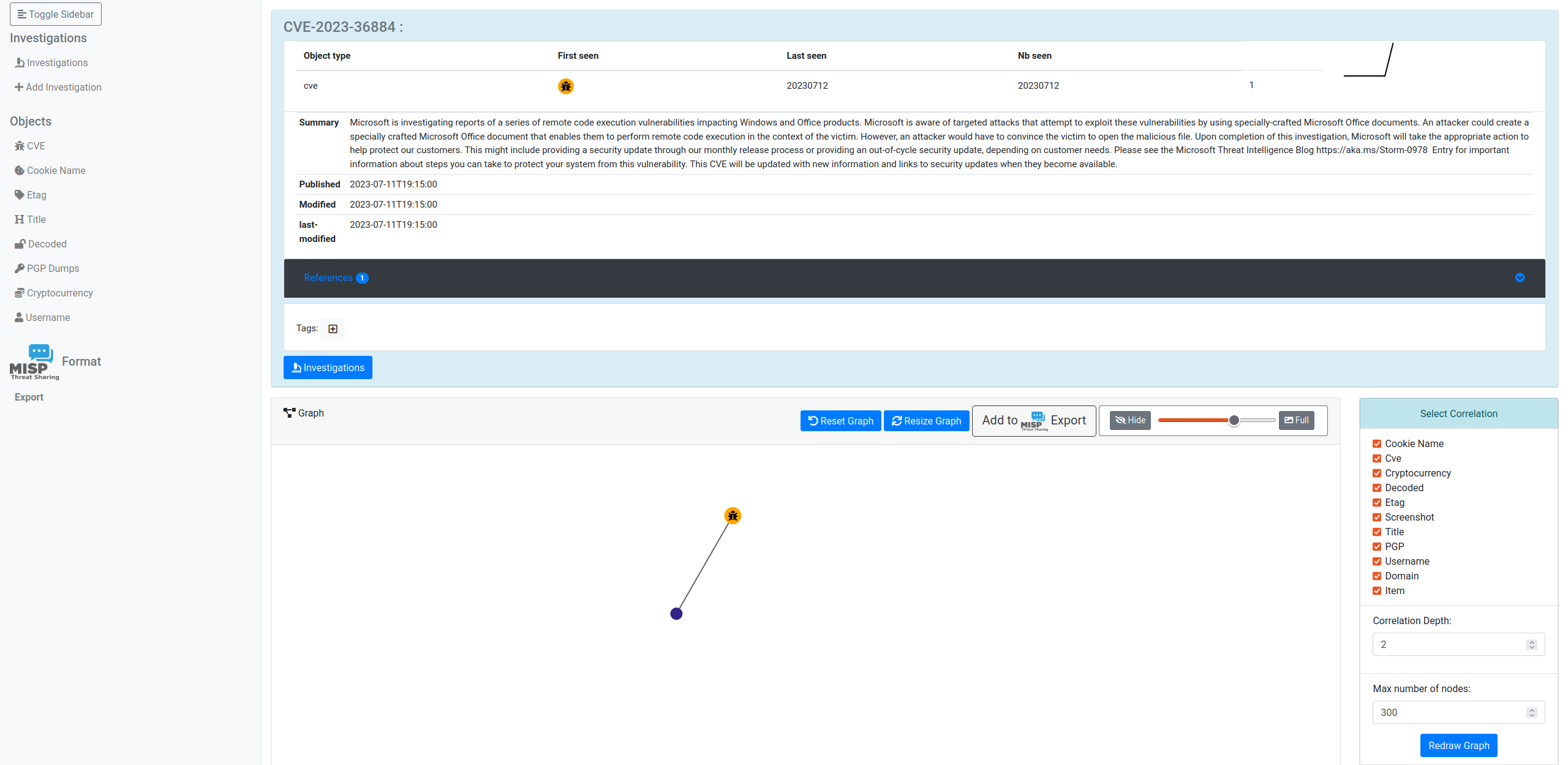
The latest release, version 5.2 of the AIL project framework, introduces several changes, fixes, and improvements. Some notable changes include the removal of old updates prior to version 5.0, a refactoring of the background updater along with the addition of the v5.2 update, and the introduction of a new etag object. The correlation graph now offers an option to hide objects/nodes and reset functionality using the “H” key. Additionally, an object comment feature has been added to investigations.
Several fixes have been implemented in this release. The environment issues in the updater and background update modules have been resolved. The crawler now includes timeouts for Unknown captures and exception handling for ping_lacus. It also performs an existence check for screenshot sets. The decoding process for downloaded files has been fixed, and the tag functionality for correlation objects has been improved. Fixes have also been made to the updater module, including the removal of old ARDB environment references. Lastly, issues with MISP event JSON export and retro hunt date search and description in the hunter module have been addressed.
In terms of contributors, Thirion Aurélien and fukusuket have made significant contributions to this release, addressing specific issues and providing fixes.
Detailed Change Log
v5.2 (2023-07-12)
Changes
-
[update] remove old updates < 5.0. [Terrtia]
-
[updater] refactor background updater + add v5.2 update. [Terrtia]
-
[crawler har] compress HAR. [Terrtia]
-
[correlation] correlation graph, add an option to hide an object/node by pressing H + reset correlation graph. [Terrtia]
-
[etag] add new etag object. [Terrtia]
-
[investigation] add object comment. [Terrtia]
Fix
-
[updater] fix env. [Terrtia]
-
[background update] fix logger. [Terrtia]
-
[crawler] add timeout to Unknown captures. [Terrtia]
-
[crawler] add exception handing for ping_lacus. [fukusuket]
-
[crawler] added existence check for screenshot set. [fukusuket]
-
[decoded] fix download file. [Terrtia]
-
[updater] fix db checker. [Terrtia]
-
[correlation tags] fix tag all objects. [Terrtia]
-
[correlation card decoded meta] mimetype + size. [Terrtia]
-
[correlation card decoded meta] mimetype + size. [Terrtia]
-
[updater] remove old ARDB env. [Terrtia]
-
[hunter + misp export] fix misp event json export + retro hunt date search and description. [Terrtia]
Other
-
Merge pull request #174 from fukusuket/fix-500-erro-when-invalid-lacus-url. [Thirion Aurélien]
fix: [crawler] add exception handing for
ping_lacus -
Merge pull request #176 from fukusuket/fix-500-error-when-crawler-screenshot-setting-off. [Thirion Aurélien]
fix: [crawler] added existence check for screenshot set
JTAN
Development of the AIL framework is co-funded by the European Union CEF program and CIRCL.
The Action will establish a Joint Threat Analysis Network, an open collaboration group of European computer security incident response teams (CSIRTs) with the focus on collecting, sharing and analysis of technical, operational and strategic threat intelligence. The purpose of this collaboration is to combine unique advantages of different teams to obtain comprehensive situational awareness and actionable information to effectively defend constituencies in each Member State, from critical infrastructure operators targeted by state-sponsored actors to individual citizens affected by cybercrime. The main part of the Action addresses gaps in the Cyber Threat Intelligence (CTI) tooling that is currently used by the national level CSIRTs in Europe. By strengthening individual tools and interconnecting them, the beneficiaries will achieve a new level of common situational awareness and they will benefit from shared knowledge and tooling.